Network Security for Businesses – Powered by NordLayer | TFG Group

As Managed Service Provider (MSP) for NordLayer, the advanced network security solution developed by the creators of NordVPN. We support UK businesses in securing their networks, enabling secure remote access, and achieving regulatory compliance — without the need for complex infrastructure. Whether you’re a small organisation or scaling enterprise, we deliver flexible, cloud-native security built for today’s hybrid workforces.
Internet Security - Modernized Network - Remote Access
- NordLayer enhances internet security and modernizes network and resource access with technical improvements aligning with the best regulatory compliance standards. Helping organizations to adopt FWaaS, ZTNA, and SWG principles, NordLayer is focused on the Security Service Edge of cybersecurity services.
Easy hardware -free Integration
- Quick and easy to integrate with existing infrastructure, hardware-free, and designed with ease of scale in mind, NordLayer meets the varying growth pace and ad-hoc cybersecurity requirements of agile businesses and distributed workforces today.
Effortless Compliance - Advanced Protection
- Enhances your security with cutting-edge tools, enable achieving regulatory compliance, Comprehensive coverage, adopting critical Security Service Edge (SSE) components, including FWaaS, ZTNA, and SWG

Use Cases
NordLayer helps businesses to secure online connections when accessing the public internet.
- Guarantee safe internet browsing for your team
- Protect your business information & sensitive data
- Organize your network into sections
- Enforce secure access with unified management
- Explore global business opportunities
- Hide your track to accessed resources
NordLayer allows IT admins to control, secure and customize remote workforce access to internal company resources.
- Controlled access to cloud tools & resources
- Team-based segmentation for safer resource accessibility
- Virtual Local Area Network (LAN)
- Remote access to different offices & devices
- All-round data breach prevention
NordLayer supports its clients pursuing various compliance certifications by providing technological solutions.
- Ensuring secure connection to isolated environments
- Encrypting data traffic at all times
- Providing efficient monitoring, logging, and auditing solutions
- Allowing only compliant devices to access internal network
- Helping implement access segmentation for resource protection
- Ensuring Zero Trust approach
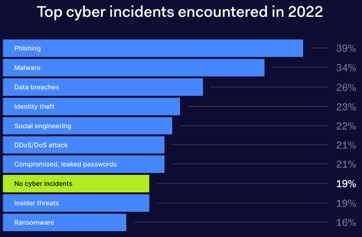
Why Does Security Matters for Businesses
Sectors
Education
Secure data erasure from donated or recycled devices, ensuring data privacy and compliance with regulations, while also enabling the reuse of IT equipment. This allows educational institutions to bridge the digital divide
Governments
Protecting end-of-life data against unauthorised access,, safe redeployment of data storage assets, firm complyiance with increased data protection and privacy requirements.
Engineering & Manufacturing
Securely data erasure from storage devices throughout the product lifecycle, ensuring data privacy and compliance with regulations during various processes like recycling, refurbishment, and end-of-life disposal. It helps manufacturers manage data securely.
Legal
Secure and verifiable data erasure from IT assets, ensuring compliance with data privacy regulations and internal policies. With BLANCCO we help law firms manage data throughout its lifecycle, from active environments to end-of-life disposal.
Financial Services
Regulatory compliance is always front-of-mind for IT organizations within financial institutions. Protecting sensitive data across its lifecycle, including verifiable, secure erasure at the time of data disposal, is a critical part of fulfilling this obligation.
Healthcare
Secure data erasure of IT assets, helping organizations comply with HIPAA regulations and other data protection standards. Healthcare providers can ensure that sensitive patient information is permanently removed from devices before disposal,
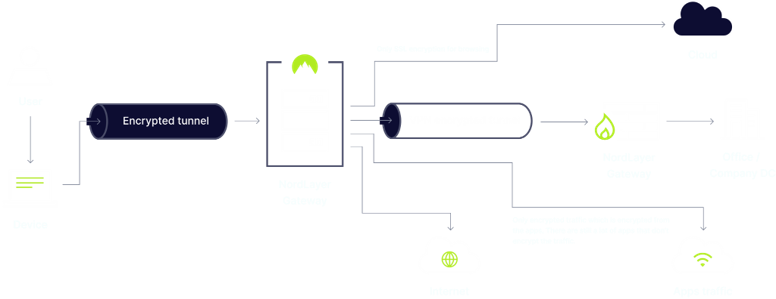
How we Secure your Team using ZTNA Model
Why to work with TFG Group
- TFG Group is an official NordLayer Managed Service Provider (MSP), offering:
- Full Flexibility: No minimum user license required — start from just one seat and scale as you grow
- Cost-Effective Licensing: Affordable monthly per-user pricing, with MSP discounts
- Expert Setup & Support: TFG provides dedicated configuration and onboarding support
- Compliance Ready: Help achieving ISO, GDPR, and SOC 2 compliance with secure network infrastructure
- Integrated Cybersecurity: Combine NordLayer with TFG’s other solutions for full-stack protection
Ready to leave cyber threats behind?
Step forward with our 14-day Free Trial


